Serverless Security 101
Since I have been using serverless rather extensively lately, I thought it would be perfect time to share what I have been learning about security in the serverless space.
So what is serverless?
Serverless architecture, or as some referred to as Function as a Service(FaaS), is an approach where software and services and built and deployed without worrying about maintaining or provisioning the physical or virtual servers.
By developing applications using serverless architectures, developers are relieved from the task of constantly applying security patches for the underlying operating system and application server. These tasks are instead the responsibility of the serverless architecture provider.
How is serverless security handled?
The following image provides a high level overview of how security responsibilities is handled between the provider and the developer in a serverless architecture
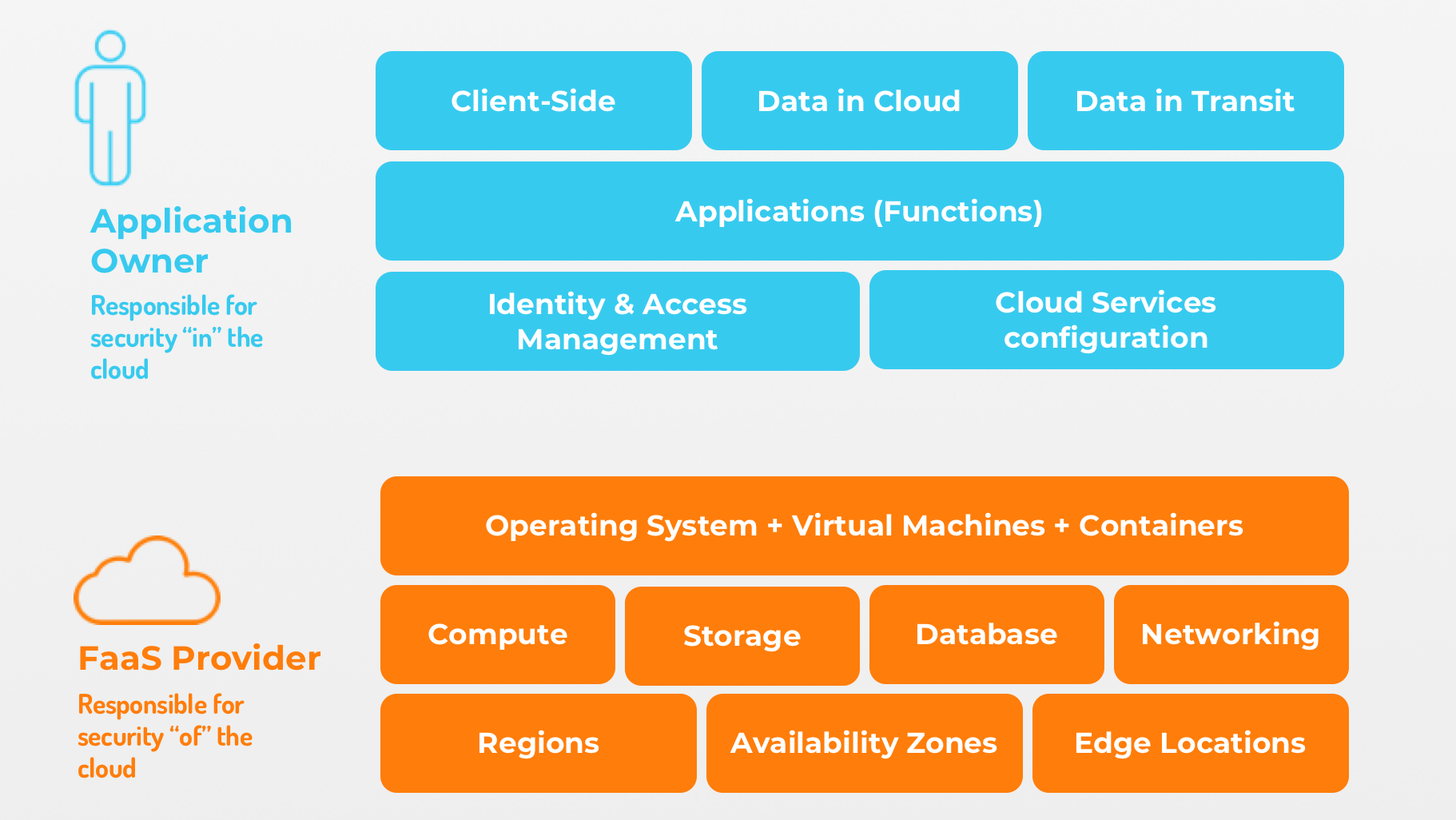
With serverless, the provider is responsible for securing infrastructure such as the the data center, network, servers, operating systems and their configurations. This leaves the developer to focuses on the application logic, code, data, and the application-layer configurations.
What are the security challenges with serverless?
While serverless architectures provides a wealth of benefits, usage of modern day serverless infrastructure also introduces a new set of challenges such as:
- Increased attack surface: Serverless functions consume data from a wide range of event sources such as HTTP APIs, message queues, cloud storage, IoT device communications and so forth. This increases the overall attack surface dramatically, especially when such messages use protocols and complex message structures - many of which are not being inspected by standard application layer protections such as Web application firewalls
- Increased system and attack surface complexity: The attack surface in serverless architectures is also relatively difficult to monitor and understand due to the unfamiliarity of this architectures by most software developers and architects.
- Inadequate security testing: Performing security testing for serverless architectures is more complex than testing standard applications, especially when these applications interact with remote 3rd party services or with back-end cloud services such as NoSQL databases, cloud storage, or stream processing services. Many automated scanning tools are currently not adapted to scanning serverless applications.
- Inability to leverage traditional security protections (Firewall, WAF, IPS/IDS): Since organizations that use serverless architectures do not have access to the server or its operating system, they are unable deploy traditional security layers such as endpoint protection, host-based intrusion prevention, web application firewalls and so forth. Existing detection logic and rules have not yet to be “translated” to support serverless environments.
How to get started securing serverless?
I would recommend that you first learn about the PureSec’s Top 10 Security Vulnerabilities for Serverless and getting hands on experience with Serverless GOAT, a deliberately insecure AWS Lambda application that teaches you how remediate each of the these security vulnerabilities.
Hope this helped you to start to understand serverless security! As always, feel free to share your comments with me on twitter @0xGuled